|

by Dr. Joseph Mercola
March 23, 2024
from
Mercola Website

Story at-a-glance
-
"Shadowgate"
reveals how a "Shadow Government" is manipulating
society from behind the scenes and using psychological
warfare tactics against the American public
-
Democrats and Republicans are equally guilty of covering
up an even bigger scandal than the fact that Obama's
administration illegally spied on and tried to frame
President Trump and others using manufactured evidence
-
The
Shadow Government consists of government contractors and
defense and intelligence officials who are stealing the
personal data collected by the NSA on all Americans, and
have privatized and weaponized its use
-
"Shadowgate"
features two whistleblowers who have spent many years
helping to develop the psychological warfare programs
that are now directed at the American people and used to
influence our elections
-
We
can protect our freedoms, first by rejecting and
abandoning companies like Google and Facebook, which are
the largest data collectors and manipulators; second, by
promoting and aiding in the effort to expose Big Tech's
manipulations; and third, by restructuring legislatures
and the government, and establishing new civil society
institutions and news media that support and promote
freedom rather than censorship and control
Banned Film Reveals
How We're Being Controlled by a 'Shadow Government'
It's not easy to wrap one's mind
around the psychological warfare tactics
being used against the American public,
but it's essential we try to do so
before it's too late.
Immediately banned on YouTube,
this important film pulls back the curtain
on how we're being manipulated
and by whom...
Most people have never even heard and there's a reason for that.
Technocrats have worked in the proverbial shadows for decades,
trying to implement a grand economic plan that is global in scope.
To beat them, we must be just as persistent in our efforts to
implement a "whole-of-society" plan of action that leads to freedom,
and I firmly believe we can.
While technocracy is an economic system and not a political system
in and of itself, it does require the undermining and erosion of the
democratic system of governance.
This is particularly true for the
United States, as our Constitution is a major barrier to the
implementation of technocracy.
The documentary far below, "Shadowgate," is produced and narrated by
Millie Weaver, an independent journalist and contributing reporter
to Infowars.
Coincidentally, Weaver and her boyfriend, Gavin Wince,
were arrested shortly after posting a trailer of the film online,
announcing its release. 1
According to Basin Report 2 and News 5 Cleveland,
3 Weaver and Wince
were both charged with,
"robbery (second-degree felony), tampering
with evidence (third-degree felony), obstructing justice
(fifth-degree felony), and domestic violence."
According to the
Portage County Sheriff's Office, the secret indictment against
Weaver and Wince was filed July 20, 2020.
'Shadowgate'
"Shadowgate," while banned on YouTube (and replaced later
on...), is available on alternative
non-censoring sites such as Bitchute and Banned.Video.
The film
reveals how a "Shadow Government" is manipulating society from
behind the scenes and using psychological warfare tactics against
the American public.
"What if I were to tell you that a small group of government
contractors were hired by government officials to frame the Trump
campaign, set him up for the Russia Collusion investigation,
provided witnesses for the impeachment hearings, and provided
administrative support services to the Department of Justice during
the Mueller investigation?
And what if it just so happened that this same group of contractors
are behind the fake news in mainstream media, influence operations
on social media, and the civil unrest nationwide, pushing the defund
the police movement?
The Obamagate scandal only scratches the
surface," Weaver says at the start of the film. 4
"Talk about a cover
story. What really happened is much more alarming."
According to Weaver, both parties - Democrats and Republicans - are
equally guilty of covering up an even bigger scandal than the fact
that
Obama's administration illegally spied on and tried to frame
President Trump and a number of other individuals using manufactured
evidence.
"Shadowgate" reveals what Weaver claims is the tactical and
operational role that,
the Shadow Government played behind the scenes
to carry out the attempted coup...
It's the things that spy novels and movies are made of, for sure.
YouTube, which pulled the film almost as soon as it was uploaded,
claims it violates the channel's policy on hate speech. I urge you
to watch it and decide for yourself whether YouTube was justified in
taking it down.
According to a Spiro Skouras summary on YouTube, the film,
"showcases
two whistleblowers who allege there is a secretive network of
government contractors which consists of government and military
insiders (both current and former) who have 'back door' access to
intelligence agencies and all of the information that they collect
on everyone including politicians and how this information is used
to blackmail powerful people to control them."
The film also,
"alleges that military psychological warfare programs
are being used against the people primarily through the mainstream
corporate media and social media to control the population."
As
noted by Weaver,
"The information presented in this video should
concern people of all political affiliations."
Who Are the Real 'Puppet Masters'?
While many career politicians are certainly part of the so-called
Shadow Government, the real puppet masters behind it all are people
that most of us are unfamiliar with.
These are the individuals
Weaver focuses on in her film.
The real Shadow Government, Weaver
says, consists of government contractors and defense and
intelligence officials.
"[Government] contractors have used
their connections, power and
influence
to create an unprecedented international criminal
enterprise
where blackmail is traded
and people's personal data is
gold."
Millie Weaver
But just how could a Shadow Government arise in the first place?
According to Weaver, the reason they've managed to operate in the
shadows and gain power for so long is because most of the actual
work in government is done by subcontractors.
This way, Freedom of
Information Act (FOIA) requests aimed at government departments turn
up very little out of the ordinary.
The real "dirt" remains hidden
in the archives of "contractors in clandestine networks."
"These contractors have used their connections, power and influence
to create an unprecedented international criminal enterprise,"
Weaver says, "where blackmail is traded and people's personal data
is gold."
Whistleblower Tore's Story
"Shadowgate" features two whistleblowers:
-
Tore, a linguist and Navy
intelligence contractor
-
Patrick Bergy, a cyber security officer
and Army PSYOP program developer
Tore claims to have been
approached by people who worked for John O. Brennan while she was
undergoing her Naval specialist training.
She was initially recruited into The Analysis Corporation's (TAC)
electronic warfare program, run by Brennan, which later morphed into
information warfare.
According to Tore, she worked with intelligence
agencies that were privately created and run.
In other words, they were not, and are not, official parts of
government.
"Unlike what most people think, our intelligence doesn't
stay within our borders or within federal buildings," she says.
Tore
worked on something called "localization strategy," which involves
finding a group of people (an organization, city, entire country or
religious group, for example) and "getting into their mind."
The object is to figure out,
...and so on.
This information is then
used to manipulate them in ways that will further your own
particular product, agenda or ideology.
The collection of information on individuals goes far beyond what
most people can imagine. As explained by Tore, the information is so
detailed, it can be easily used to blackmail or hurt just about
anyone.
As an example,
if they know you have an old hockey injury, they know
where to hit you in order to cause the most pain and damage, were a
physical attack to be ordered against you.
They also know what you fear most, and who the people are in your
social circle, and who might be best able to influence you.
Tore
claims she actually helped train the algorithms for the program Bergy developed, using these localization strategies.
Whistleblower Patrick Bergy's
Story
For eight years, Bergy worked for the Dynology Corporation, owned by
former President Obama's national security adviser, Gen. James
Jones.
Bergy worked directly under the General's son, Jim Jones...
From 2007 to 2010, Bergy's primary focus was the development of
interactive internet activity capabilities, including hacking
capabilities.
He also claims to have worked on information operations, so-called
"influence operations."
Like Tore, Bergy worked on intelligence
operations run by private companies. ShadowNet is the commercial
version of an interactive internet activities (IIA) weapon, which
Bergy developed.
Fake news, false news stories and the falsified dossier used to
frame the Trump campaign are all characteristic of IIA, which Bergy
refers to as "social media psychological warfare."
According to Bergy, Dynology has been conducting IIA operations for the
Department of Defense since 2007.
The ShadowNet program Bergy developed was based on the localization
strategies that Tore worked on. As explained by Bergy, it can very
effectively control large groups of people by pushing the right
hot-buttons.
The COVID-19 hysteria and Black Lives Matter
riots are
two real-world examples of what this kind of PSYOP program can
accomplish, Bergy says.
Interestingly, while these kinds of psychological operations were
initially conducted by individual operators or agents, much of it
has since been taken over by artificial intelligence, which executes
the programming based on the behavioral profile targets the
programmer selects.
As noted by Bergy, with enough information about any given
individual, you can predict how they will react to a given stimulus
with a high degree of accuracy.
So, has this technology been used to
influence
American elections? According to Bergy,
yes...!
While American tax payers paid for the development of the program,
Dynology holds the intellectual property and has been using it
against the American people for years, propping up certain
politicians and undermining others.
How the Shadow Intelligence
Apparatus Works
As explained in the film, Section 702 of the Foreign Surveillance
Act allows government to spy on American citizens with a warrant
from the foreign intelligence surveillance (FISA) court.
The upstream data collected by
the NSA on all Americans is only
stored for 72 hours before being dumped.
We're talking about all
phone calls, texts, emails, social media interactions, online
activity, facial and voice recognition data and much more, of all
Americans...
But what's actually happening is that this data stream is being
duplicated, stored indefinitely and privatized by companies such as,
The Global Strategies Group is a hub for this information, according
to Tore.
So, while these companies claim to be consulting firms,
they're not actually consulting at all. They're stealing everyone's
data and using it against us in psychological operations designed to
move society in one direction or another.
Tore claims she worked for Brennan at The Analysis Corporation and
the Global Strategies Group, and that she conducted what were later
described as "hacks" at the request of higher-ups.
According to
Tore, Brennan's modus operandi is that when he wants a piece of
information about someone - or if he wants to alter data relating to
a target - he simply blames it on hackers.
According to the whistleblowers featured in this film, these
privatized intelligence companies
helped get Barack Obama elected
using sophisticated internet influence operations.
The film also reviews a variety of other scandals that have emerged,
and how the truth has been spun and covered up, including the
illegal "hacking" and surveillance of the U.S. Congress, which
occurred while Brennan was director of the CIA.
Private Intelligence Companies Dictate the News
Have you ever wondered who creates the talking points being
regurgitated across dozens if not hundreds of news outlets on a
daily basis?
According to Bergy, this is the work of this network of
privatized intelligence companies, utilizing tools such as ShadowNet.
When asked whether IIA has been used against President
Trump, Bergy
replies, "Absolutely"...
According to Bergy, the Steele dossier was
manufactured and used as a weapon to frame Trump and remove him from
office.
Tore agrees. They have been and continue to use military-grade
psychological warfare tactics against the president.
She also
discusses the IIA strategies employed in an effort to get
Hillary
Clinton elected.
Backdoor Access to All Data
According to Tore, she had backdoor access to all data and has
personally viewed the kind of data collected on political figures.
She's also seen how that illegal data collection is used.
If someone steps out of line, it's used to blackmail them back into
lockstep with whatever the agenda might be. And, according to Tore,
deep state Shadow Government actors,
are equally spread between the
two political parties of the United States...
She also claims the Cambridge Analytica scandal was an IIA operation
to make it appear as though Russia helped Trump win the election.
This way, the Russia collusion hoax narrative would "stick" better.
In reality, the PSYOP was conducted by the privatized intelligence
network.
There's a lot to digest in this film, but I urge you to set aside
the hour and a half to do so.
It answers many questions, revealing
how government contractors are subverting our justice and political
systems to further their own hidden aims.
At the heart of it all is
Gen. Jones.
According to Tore and Bergy, Jones, who heads up Clearforce, took
ShadowNet and made it what it is today:
a PSYOPs weapon used
against the American people and the Shadow Government's enemies...
Jones is also the chairman of the board of the Atlantic Council, and
according to Bergy, one of the first things he did after being
appointed chairman was to enter the Atlantic Council into a
partnership
with Facebook,
"to restore election integrity worldwide."
In other words,
Facebook is partnered with the owner of ShadowNet,
one of the greatest
PSYOP weapons in the world...!
To think this
partnership will actually prevent election interference would be
delusional, as its purpose is to do the complete opposite.
The Ultimate
Surveillance State Is Near Completion
"More stuff is fake and fabricated now, in the news, than is
actually real," Bergy says.
The reason for this is because IIA is in
full force.
As explained by Tore, IIA is essentially an AI program
that tells you what you need to do, what message you need to put
out, in order to get a specific outcome. It's now running
continuously.
Similar technology is even being used to undermine our judicial
system.
According to Tore and Bergy, a program will select jurors
most likely to either acquit or find a defendant guilty (depending
on the desired outcome).
While jury selection process is supposed to be random, it's not.
From that initial pool, jurors are then selected by the attorneys.
But they were all non-randomly preselected in the first place, based
on their proclivities, ways of thinking and behaving, and their
belief systems.
And, the data used to make that selection was
siphoned from the NSA by these private intelligence companies.
"This is the biggest and boldest move toward the ultimate
surveillance state ever made, and it's near completion",
...Weaver
says, noting that in order to effectively micromanage the
surveillance and manipulation of the global population, the
technology must be integrated with AI and the Internet of Things,
and that is already underway.
Part of the plan is to automate policing using robots and other
technologies.
According to Weaver, this may be why there's now such
a strong push to defund police departments across the U.S. This
would allow the Shadow Government players to directly benefit by
offering up new AI technologies to take over police functions.
Again, I hope you take the time to watch "Shadowgate."
Then, if you
haven't done so already, listen to my interview with Patrick Wood,
featured in "The Pressing Dangers of Technocracy."
It's really
crucial for everyone to start wrapping their minds around what's
happening, and what's in store for us if we don't fight back and
demand the restoration of privacy, both online and off.
Time to Break the IIA Programming
The good news is, there's still time to break the IIA programming.
How do we do it?
First, by rejecting and abandoning the surveillance
state's primary data collection centers -
Google and
Facebook. Both
have tremendous, hidden surveillance powers, act as censoring
agencies for the technocratic cabal, and have the power to
manipulate public opinion en masse.
For example, Robert Epstein, Ph.D.,
has demonstrated that Google has
the ability to shift voting preferences among undecided voters by a
whopping 48% to 63%, and the power to determine 25% of global
elections.
What's more, this manipulation is entirely undetectable
and untraceable.
Epstein is now working to make Google's
manipulations transparent, through an organization called Feed the
Watchdogs.
They have more than 13,000 watchdogs who monitor Big Tech for
election bias 24/7 by collecting the ephemeral data that Google and
other Big Tech companies are sending out to manipulate voters.
You
can help in this indispensable work by making a one-time or
recurrent donation.
For just $25, you can sponsor one month of data
collecting...
At the time of this writing, Feed the Watchdogs had captured nearly
80,000 pages sent by Google, Facebook, YouTube and others to
manipulate Americans.
As their tactics become provable and more
well-known, they'll have little choice but to quit.
Of course, I
believe the best strategy is to ditch them all before then.
Say Goodbye to Google
Quitting Facebook is a simple enough affair.
Just cancel your
account...
Evading Google, however, can be a bit more complicated,
as
their products span a wide range of products.
For a comprehensive purge, be sure to eliminate
all of the following:
Google Chrome browser
Uninstall Google
Chrome and use Brave or Opera instead. Everything you do on
Chrome is surveilled, including keystrokes and every webpage
you've ever visited. Brave is a great alternative that takes
privacy seriously.
Google search engine
Stop using Google search engines or any
extension of Google, such as Bing or Yahoo, both of which draw
search results from Google. Instead, use a default search engine
that offers privacy, such as Presearch, Startpage, DuckDuckGo,
Qwant and many others.
Gmail
Close your Gmail account and switch to a secure email
service like ProtonMail. If you have children, don't transfer
their student Google account into a personal account once
they're out of school.
Google Docs
Ditch Google Docs and use another alternative such
as Zoho Office, Etherpad, CryptPad, OnlyOffice or Nuclino, all
of which are recommended by NordVPN.5
Google apps
Delete all Google apps from your phone and purge
Google hardware. Better yet, get a de-Googled phone. Several
companies now offer them, including Above Phone.
Avoid websites that use Google Analytics
To do that, you'll
need to check the website's privacy policy and search for
"Google." Websites are required to disclose if they use a
third-party surveillance tool. If they use Google Analytics, ask
them to switch!
Google Home
Don't use Google Home devices in your house or
apartment. These devices record everything that occurs in your
home, both speech and sounds such as brushing your teeth and
boiling water, even when they appear to be inactive, and send
that information back to Google. The same goes for Google's home
thermostat Nest and Amazon's Alexa.
Android cell phones
Don't use an Android cellphone, as it's
owned by Google.
Siri
Ditch Siri, which draws all its answers from Google.
Fitbit
Don't use Fitbit, as it has been purchased by Google
and will provide them with all your physiological information
and activity levels, in addition to everything else that Google
already has on you.
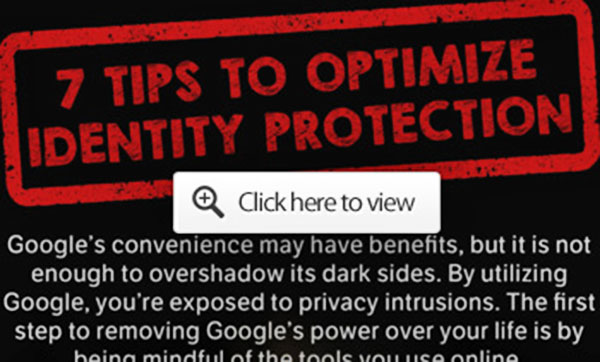
Additional tips to protect your privacy are
included in the following graphic, such as making sure you're using
a secure messaging system and virtual private network (VPN) for your
web searches.
Building a
Whole-of-Society Solution
In addition to getting yourself (and as many of your friends and
family as possible) off Google and Facebook, we also need to build a
society that values freedom above all.
According to the Department of Homeland Security, misinformation
online is a whole-of-society problem that requires a
whole-of-society solution.
By that, they mean that four types of
institutions must fuse together as a seamless whole:
-
Government institutions, which provide
funding and coordination.
-
Private sector institutions that do the censorship and dedicate
funds to censorship through corporate-social responsibility
programs.
-
Civil society institutions (universities, NGOs, academia,
foundations, nonprofits and activists) that do the research, the
spying and collecting of data that are then given to the private
sector to censor.
-
News media/fact checking institutions, which put pressure on
institutions, platforms and businesses to comply with the
censorship demands.
To effectively combat the globalist technocrats'
takeover, we need to do the same. Here, an organization called
Foundation for Freedom Online (FFO) comes to the rescue.
FFO educates people about this structure, and the ways in which
legislatures and the government can be restructured, how civil
society institutions can be established, and how news media can be
created to support and promote freedom rather than censorship.
To
learn how you can be part of the solution, check out foundationforfreedomonline.com.
I firmly believe that we can turn this situation around, if for no
other reason than the fact that there are some eight billion of us
who want freedom, while those who seek to enslave us number in the
thousands, or tens of thousands at the most.
Either way, they're
clearly outnumbered.
But we need to spread the word, and help our friends and family
understand how important our decisions are.
We either support the
network that seeks to take our freedom, or the network that seeks to
protect it...!
The Power of
Choice
Lastly, I encourage you to seek Joy.
At the end of the day, that's
what life is all about. It's all too easy to fall into the trap of
feeling like the sky is falling. What we're facing is serious, yes.
But we can overcome it.
And, I believe that Joy-seeking may be a
crucial component to winning.
Why?
Because when you focus on what brings you Joy, everything else
falls into place.
New ideas arise.
New solutions.
And that's
precisely what we need.
We need a world full of joyful, inspired
people who are living their dreams, and in so doing, end up bringing
new solutions to the world...!
Video
Also
HERE,
HERE,
HERE and
HERE...
Sources and References
|