|
Credit: John Schnobrich
on Unsplash
Opportunistic agility is running rampant
among hackers
and scammers...
Ransomware on
cloud servers, hijack attempts on IoT gadgets and business email
compromise (BEC)
attacks increased in volume as well as sophistication over the
course of
Q3 2020.
Understandably, organizations prioritized keeping the lights on.
Millions of people moved online, including individuals without much experience of working or shopping through the internet, and with equally poor cybersecurity awareness.
There's no debate about whether hacking and other malicious cyberattacks have increased.
McAfee alone reports that malware grew 1,902 percent over the past four quarters, and the company's user base has been seeing an average of 375 new threats per minute during the pandemic.
It's clear that cybercrime is flourishing in these conditions.
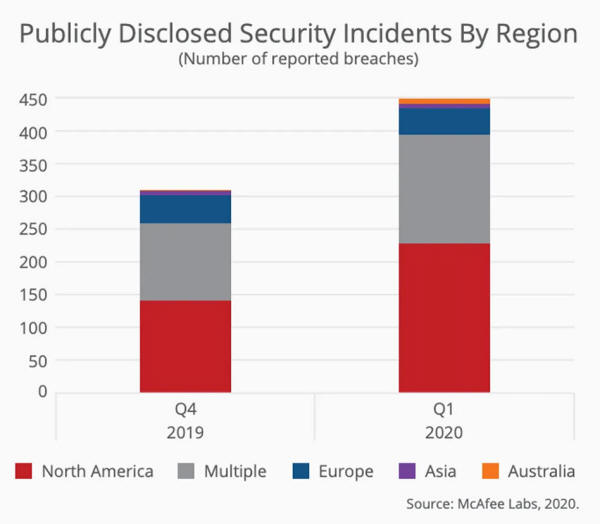
Credit: McAfee
But beyond the many reports that cybercrime has surged, there's been proportionately little talk about how it's changed.
Once everyone got situated in their home offices and their company's security teams started taking the appropriate measures, how did the attackers adjust?
Here are four ways that cybercrime has visibly adapted to the changing conditions of 2020.
Deploying pandemic-related attack strategies
One of the notable ways that attacks were especially effective at the start of the pandemic was the manner in which they directly took advantage of the confusion caused by the situation.
COVID-19 related phishing emails raised phishing attacks overall by 68 percent.
There was also a marked uptick in business email compromise (BEC) attacks, where the criminal masquerades as a legitimate company and attempts to convince the victim that the coronavirus chaos forced them to change their banking details.
Cybercriminals have adjusted their targeting and tactics to follow the spread of COVID-19, with the spike beginning in Asia before shifting to Europe and the U.S. Now, as people are returning to work, phishing emails and malware have switched gears
Instead of claiming to educate you about the virus, they are disguised as guides to helping workers return safely to the office.
In this vein, malware, mobile malware and fileless malware have skyrocketed, using pandemic-related topics to play on people's fears and lure them to malicious URLs.
Alex Tarter estimates that half of all COVID-19-related domain names created since December 2019 were set up with the purpose of injecting malware, with many of these domains spoofing content from genuine websites in order to mask their intent.
Aiming at broader targets
Another distinct trend is the shift to a broader attack surface.
As work moved out of "on-premises" network environments, bad actors have followed us onto the cloud, so cloud-related breaches have increased.
Protecting your server isn't sufficient; you need to connect all the dots and cover every connected device, because your cloud-connected printer is the backdoor to your entire organization.
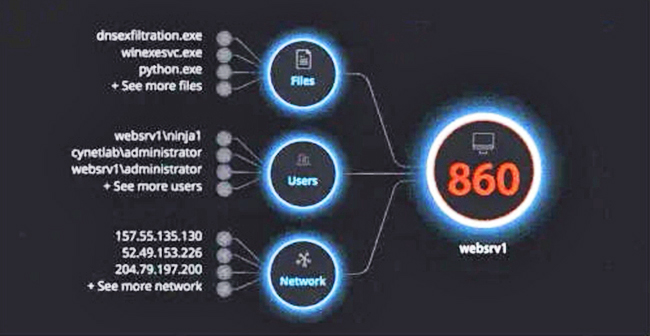
Cybercriminals have long since woken up to the fact that IoT devices are often the weakest links in any system.
IoT-focused attacks have grown in number and in impact, with a 46 percent rise in the number of attacks on smart homes, smart enterprises, and control systems that are connected to critical infrastructure.
Credit: Cynet
It's no longer enough to simply protect your endpoints...
Iin 2020, you need to deploy a next-generation extended detection and response solution like Cynet XDR, which continuously and proactively monitor the entire ecosystem for attacks across all endpoints and networks and can automate blocking actions.
Taking advantage of urgency and pressure
Cybercriminals are taking advantage of the pressure that organizations are under to remain operational by expanding ransomware attacks, which doubled from 200,000 in Q1 2020 to 400,000 in Q2.
Health centers are a popular target, because hackers know that they are overwhelmed with critical patients and can't afford the time it will take to resolve the attack, so they are more likely to give in and pay the ransom than struggle to combat and cure it.
A few weeks ago in Germany, a patient was unable to receive care when a ransomware attack on Düsseldorf University Hospital disrupted the emergency care unit, forcing them to transfer her to another hospital to receive critical care.
The patient died during the journey, a cybercrime first.
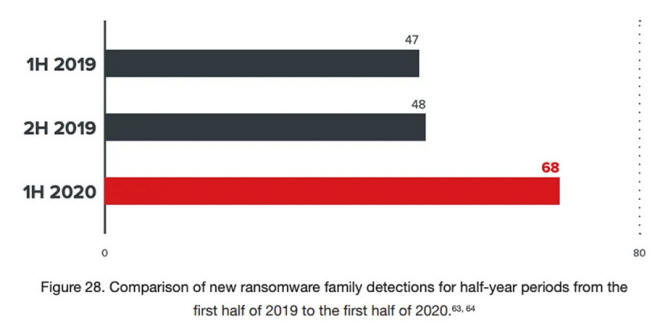
Credit: Trend Micro
New ransomware families are emerging, using more sophisticated, phased attack strategies that are more difficult to rectify.
Trend Micro has identified a 36 percent jump in new ransomware families, compared with the same period in 2019.
Hackers know that IT and security teams are operating remotely, without access to their usual tools and processes and often without experience in dealing with an attack remotely, which handicaps their ability to resolve it quickly.
Exploiting remote work vulnerabilities
Hackers have been quick to respond to the sudden rush to remote working.
In the urgency of the moment, many companies implemented trusted VPN services for employees working from home, or set up a remote desktop, without configuring them properly, thereby opening the doors to hackers.
In March, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) alerted businesses to elevated risks of VPN abuse.
A number of cloud tools are poorly protected. Zoom, for example, has become a lifeline for businesses and schools, but it has serious security vulnerabilities.
It's no coincidence that individuals and educational organizations have been the targets of so many cyber attacks during the pandemic:
Shadow IT use rose when employees sent home from the office had no choice but to use their personal laptops for sensitive work-related tasks, but these devices are rarely protected as well as an office computer.
Phishing attacks rose in part because many employees switched to work remotely almost overnight, without any training to independently recognize phishing scams.
The average employee isn't equipped to deal with them, and at home there's no security team on hand to immediately respond to questions and defuse the threat.
Cybercrime adapted quickly to COVID-19 chaos
The coronavirus pandemic increased chaos in the world, and that presented a golden opportunity to malicious actors and hackers of all types.
COVID-19 saw cybercrime shift to cynically exploit fears about the pandemic, take advantage of hasty shifts to remote working, attack overstretched critical infrastructure like health industries, and aim at broader targets across organizations.
IT teams can't afford to fall behind as the ongoing struggle with cybercrime enters a new phase.
|