|
September 27, 2011 from Salon Website
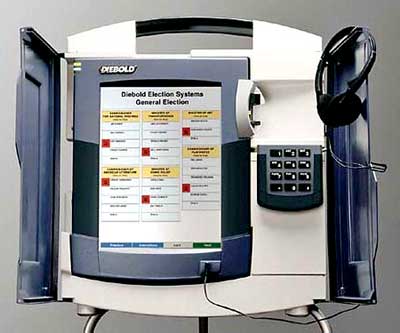
A laboratory shows how an e-voting machine used by a third of all voters
can be easily manipulated It could be one of the most disturbing e-voting machine hacks to date.
Voting machines used by as many as a quarter of American voters heading to the polls in 2012 can be hacked with just $10.50 in parts and an 8th grade science education, according to computer science and security experts at the Vulnerability Assessment Team at Argonne National Laboratory in Illinois.
The experts say the newly developed hack could change voting results while leaving absolutely no trace of the manipulation behind.
The Argonne Lab, run by the Department of Energy, has the mission of conducting scientific research to meet national needs.
The Diebold Accuvote voting system used in the study was loaned to the lab’s scientists by VelvetRevolution.us, of which the Brad Blog is a co-founder.
Velvet Revolution received the machine from a former Diebold contractor.
Previous lab demonstrations of e-voting system hacks, such as Princeton’s demonstration of a viral cyber attack on a Diebold touch-screen system - as I wrote for Salon back in 2006 - relied on cyber attacks to change the results of elections.
Such attacks, according to the team at Argonne, require more coding skills and knowledge of the voting system software than is needed for the attack on the Diebold system.
Indeed, the Argonne team’s attack required no modification, reprogramming, or even knowledge, of the voting machine’s proprietary source code. It was carried out by inserting a piece of inexpensive “alien electronics” into the machine.
The Argonne team’s demonstration of the attack on a Diebold Accuvote machine is seen in a short new video shared exclusively with the Brad Blog [posted below].
The team successfully demonstrated a similar attack on a touch-screen system made by Sequoia Voting Systems in 2009.
|