|
15 March 2014 from TheIntercept Website
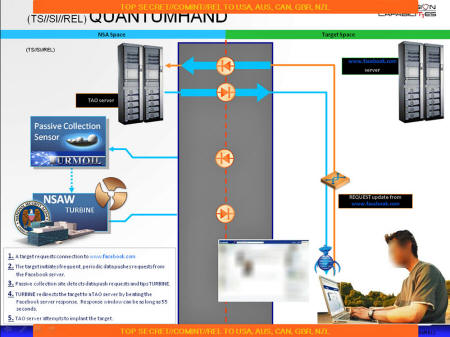
A top-secret NSA presentation reveals how the agency used Facebook to hack into targeted computers for surveillance.
On Wednesday, Glenn Greenwald and I revealed new details about the National Security Agency's efforts to radically expand its ability to hack into computers and networks across the world.
The story has received a lot of attention, and one detail in particular has sparked controversy:
This revelation apparently infuriated Facebook founder Mark Zuckerberg so much that he got on the phone to President Barack Obama to complain about it.
That wasn't all.
Wired ran a piece saying that the NSA's widespread use of its malware tools,
Slate noted that the NSA's hacking platform appears to be,
Meanwhile, Ars Technica wrote that the surveillance technology we exposed "poses a risk to the entire Internet."
In response, the NSA has attempted to quell the backlash by putting out a public statement dismissing what it called "inaccurate" media reports.
The agency denied that it was,
The statement follows a trend that has repeatedly been seen in the aftermath of major disclosures from documents turned over by NSA whistleblower Edward Snowden, in which the NSA or one of its implicated allies issues a carefully worded non-denial denial that on the face of it seems to refute an allegation but on closer inspection does not refute it at all.
Prior to publishing our story, we asked the NSA to explain its use of Facebook to deploy malware as part of a top-secret initiative codenamed QUANTUMHAND.
The NSA declined to answer all of our questions or offer context for the documents. We went into meticulous detail in our report, which went through a rigorous fact-checking process because of the gravity of the revelations.
What we reported, accurately, was that the Snowden files showed how the agency had in some cases,
The source for that detail was not plucked from thin air; it was rooted in multiple documents that refer to the technique in action, including the internal NSA animation that we published.
A particular short excerpt from one of the classified documents, however, has taken on new significance due to the NSA's statement. The excerpt is worth drawing attention to here because of the clarity of the language it uses about the Facebook tactic and the light it shines on the NSA's denial.
Referencing the NSA's Quantum malware initiative, the document, dated April 2011, explains how the NSA "pretends" to be Facebook servers to deploy its surveillance "implants" on target's computers:
It is difficult to square the NSA secretly saying that it,
Either way, the language used in the NSA's public statement seems highly misleading - which is why several tech writers have rightly treated it with skepticism.
The same is true of the NSA's denial that it has not "infected millions of computers around the world with malware" as part of its hacking efforts. Our report never actually accused the NSA of having achieved that milestone.
Again, we reported exactly what the NSA's own documents say:
Only a decade ago, the number of implants deployed by the NSA was in the hundreds, according to the Snowden files.
But the agency now reportedly manages a network of between 85,000 and 100,000 implants in computers systems worldwide - and, if TURBINE's capabilities and the NSA's own documents are anything to go by, it is intent on substantially increasing those numbers.
The rapid proliferation of these hacking techniques in the past decade, under cover of intense secrecy, is extraordinary and unprecedented. The NSA insists in its denial that its hacking efforts are not "indiscriminate."
Yet how the agency defines "indiscriminate" in this context remains unclear.
The Intercept asked the NSA to clarify some of these issues for this post.
The agency declined to answer all of these questions.
Instead, spokeswoman Vanee' Vines said that the NSA stood by its original statement, adding only that,
The NSA's outgoing chief has claimed that the agency supports increased transparency in the wake of the Snowden leaks - but its response to the latest disclosures illustrates that it is failing to live up to that commitment.
If the NSA truly wants to gain citizens' trust, it should rethink its slippery public relations strategy.
A good first step would be to stop issuing dubious denials that seem to sit so starkly at odds with what its officials were saying in secret when they thought nobody would ever learn about what they were doing.
|