A new slide leaked
by Edward Snowden shows
where the NSA infected more than 50,000 computer networks worldwide with
malware, according to Dutch media outlet NRC.
The NSA management presentation slide from
2012 shows a world map spiderwebbed with "Computer Network Exploitation"
access points in more than 50,000 locations around the globe.
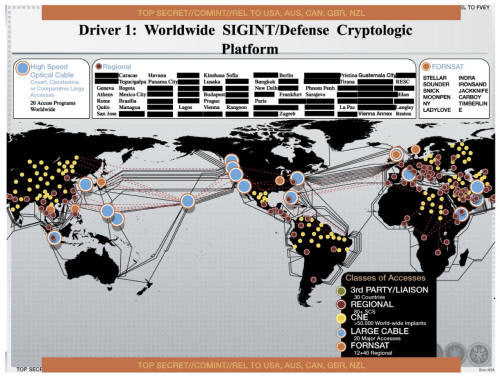
Like all the slides we've seen so far, this
one is unlikely to win a Powerpoint beauty pageant anytime soon.
Not that this should deter anyone from the
profoundly disturbing implications of a US government malware map being
reported by a Dutch news agency - to which the US government gave a "no
comment."
Translated
from Dutch:
The American intelligence service - NSA
- infected more than 50,000 computer networks worldwide with
malicious software designed to steal sensitive information.
Documents provided by former NSA
employee Edward Snowden and seen by this newspaper, prove this.
(...) The NSA declined to comment and
referred to the US Government. A government spokesperson states that
any disclosure of classified material is harmful to our national
security.
On the
NSA's Computer Network Operations program description page it
describes CNE as,
"Includes enabling actions and
intelligence collection via computer networks that exploit data
gathered from target or enemy information systems or networks."
In an article dated August 29, 2013, The
Washington Post
reported on the NSA's "hacking unit" called
Tailored Access
Operations (TAO).
The Post wrote:
According to a profile by
Matthew M. Aid for Foreign Policy, it's a highly secret but
incredibly important NSA program that collects intelligence about
foreign targets by hacking into their computers, stealing data, and
monitoring communications.
(...) Dean Schyvincht, who claims to
currently be a TAO Senior Computer Network Operator in Texas, might
reveal the most about the scope of TAO activities.
He says the 14 personnel under his
management have completed,
"over 54,000 Global Network Exploitation (GNE)
operations in support of national intelligence agency
requirements."
This is one letter away from being exact.
On the NSA's
network
ops page, there is no program with the acronym GNE - only CNE and,
-
Computer Network Attack (CNA): Includes
actions taken via computer networks to disrupt, deny, degrade, or
destroy the information within computers and computer networks
and/or the computers/networks themselves.
-
Computer Network Defense (CND): Includes
actions taken via computer networks to protect, monitor, analyze,
detect, and respond to network attacks, intrusions, disruptions, or
other unauthorized actions that would compromise or cripple defense
information.
Across the slide top and bottom a stripe
reads,
"REL TO USA, AUS, CAN, GBR, NZL."
These are
the so-called "Five Eyes" nations
- which include,
-
the U.S.
-
U.K.
-
Canada
-
Australia
-
New Zealand
Last week, the very same
"Five Eyes"
nations moved to oppose the United Nation's anti-surveillance,
right-to-privacy draft resolution called "The right to privacy in
the digital age".
Security researchers online are speculating
that telecoms were the most likely targets for the malware.
They may not be too far off the mark.
NRC cites an example of
Britain's
intelligence service GCHQ, being found to use spoofed LinkedIn pages to
install surveillance malware on target computers in Belgium telecom,
Belgacom (translated):
One example of this type of hacking was
discovered in September 2013 at the Belgium telecom provider
Belgacom.
For a number of years the British
intelligence service - GCHQ - has been installing this malicious
software in the Belgacom network in order to tap their customer's
telephone and data traffic.
The Belgacom network was infiltrated by
GCHQ through a process of luring employees to a false Linkedin page.
NRC concludes its explosive article by
telling us that the Dutch government's intelligence services has its own
hacking unit, but is prohibited by law from performing the type of
operations the NSA appears to have done in the CNE slide.
Unlike the feeling here in the US, where
it's starting to feel like an ordered state against which a
transgression can be measured has nearly vanished, and is almost
forgotten.
Despite U.S. Opposition, U.N. Pushes
Forward...
Surveillance Bill of Rights
by Jon Queally
staff writer
November 22, 2013
from
CommonDreams Website
The so-called "Five Eyes"
countries
overwhelmed by international unity
on the right to protection from
spying

'Stop spying on us...'
That is the message being sent by the
majority of nations to the world's most powerful and aggressive
surveillance states.
An effort to move forward on the United Nation's draft agreement on the
right to privacy in the digital age met opposition this week from the
so-called "Five Eyes" nations, which
includes,
-
the U.S.
-
U.K.
-
Canada
-
Australia
-
New Zealand,
...but the efforts to dilute the pact were
largely overcome by overwhelming support from the more than one hundred
nations demanding stronger protections in the wake of revelations about
the behavior of the NSA and other intelligence agencies.
As the Guardian
reports:
The resolution, titled ‘The right to
privacy in the digital age’, was hammered out at a committee open to
all 193 UN members. It represents the biggest show of international
opinion yet in response to the revelations about mass surveillance
exposed by whistleblower Edward Snowden.
Brazil and Germany co-sponsored the resolution following disclosure
that the the NSA eavesdropped on,
Other sponsors include:
-
Austria
-
Bolivia
-
North Korea
-
Ecuador
-
France
-
Indonesia
-
Lichtenstein
-
Peru
-
Switzerland
-
Spain
-
Luxembourg
-
Uruguay
A vote at the UN general assembly on the
resolution is scheduled for Tuesday but only if a member state calls
for one.
Otherwise it will pass automatically as a consensus
measure. The US may decide against calling for a vote rather than
find itself, as diplomats and officials based at the UN predict, in
a tiny, embarrassing minority.
“There is a head of steam building up behind this draft resolution.
It is a basic rights issue and these attract a lot of support,” a UN
official said.
This week, human rights groups online
privacy advocates set a joint letter to the UN urging the stronger
language and protections.
Signed by the groups,
...the
letter read in part:
The right to privacy is central to who
we are as humans and is enshrined in the Universal Declaration of
Human Rights and the International Covenant on Civil and Political
Rights.
It protects us from unwarranted
intrusions into our daily lives, allows us to speak freely without
fear of retribution, and helps keep our personal information,
including health records, political affiliations, sexual
orientation, and familial histories, safe.
Indiscriminate mass
surveillance, which tramples individuals’ right to privacy and
undermines the social contract we all have with the State, must come
to end immediately. [...]
As negotiations continue on this draft resolution, we are deeply
concerned that the countries representing the “Five Eyes”
surveillance alliance - the United States, Canada, New Zealand,
Australia and the United Kingdom - have sought to weaken the
resolution at the risk of undercutting their own longstanding public
commitment to privacy and free expression.
And the groups offered these specific point
to the world body:
-
Privacy is intrinsically linked to
freedom of expression and many other rights
-
The mere existence of domestic
legislation is not all that is required to make surveillance
lawful under international law
-
Indiscriminate, mass surveillance is
never legitimate as intrusions on privacy must always be
genuinely necessary and proportionate
-
When States conduct extraterritorial
surveillance, thereby exerting control over the privacy and
rights of persons, they have obligations to respect privacy and
related rights beyond the limits of their own borders
-
Privacy is also interfered with even
when metadata and other third party communications are
intercepted and collected
Whether or not the draft agreement is
adopted, the ability of the UN to curb the worst practices of powerful
intelligence agencies from one country illegally spying on the citizens
of another will remain a contentious issue.
As the Guardian reports, citing a leaked draft of a U.S. briefing paper
on the UN resolution, because the U.S.,
"does not consider its surveillance
activities illegal, it does not have a problem with condemning
illegal surveillance."


